How Managed IT Security Services (MISS) differ from existing IT Support or standard Managed IT Services?
Whether your business employs an internal IT team or an external Managed Service Provider (IT MSP), in most cases, these teams do not include highly skilled, dedicated IT Security specialists. Very few MSP contracts include or address specific IT security or cyber security controls or mechanisms. An IT team or MSP’s core mandate is focused on providing service continuity to the organisation, often with security being an afterthought or pushed lower down the priority list. This leaves potential security gaps in information systems that can leave an organisation vulnerable to compromise or a data breach.
Recent reports from AustCyber, and other industry professionals, estimate a shortfall of 20,000-30,000 people in Australia alone. With a chronic shortage of experienced IT and cyber security professionals within the industry, experienced security professionals are hard to find, expensive to recruit and even harder to retain long term.
The Changing Landscape
Over the last decade, cloud adoption has grown exponentially, and the increased footprint of systems and data has added complexity. The attack surface is constantly evolving due to this rapid change, leaving IT teams struggling to upskill while delivering on day-to-day operations, business continuity requirements or new projects.
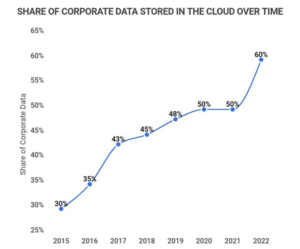
(Cloud Adoption over time taken from 25 Amazing Cloud Adoption Statistics [2022] – Zippia)
Even organisations committed to improving their IT security and cyber security postures witness priority mitigations, often going months or years without progress.
As data breaches persist and ransomware claims explode, Cyber Insurance companies are now requiring organisations to demonstrate intent. Ticking boxes is no longer acceptable with many requiring proof of certain security controls such as conformity to the Essential Eight, password management, enforced multi-factor authentication (MFA) and various other controls to obtain cover or be successful with claims.
Additionally, as organisations become more cyber aware, they too are requiring those whom they deal with in a business capacity to demonstrate an accepted level of cyber maturity that mitigates their Supply Chain Risk.
What is MISS?
MISS is a portfolio of specific managed IT security services designed to protect businesses from the most common risks associated with configurations, security controls & settings, deployments, and migrations which are often missed, omitted, overlooked or where there is a lack of specialist knowledge. MISS is an ongoing journey that will significantly enhance your IT security posture, whilst complimenting your cyber security maturity journey.
The fully managed service is designed to act as an extension of your existing capabilities, and will deliver a strong security uplift across your organisation. We carefully tailor it towards your business’s specific digital environment, requirements, risk appetite and budget and where possible, our team can also attend your premises to work alongside your internal or external IT teams, sharing knowledge and expertise.
The service seeks to identify any risks or gaps in your technology and digital environments, producing a detailed roadmap of remediation advice. Our team will work collaboratively with your internal or external team towards addressing this roadmap, in order of priority, over the term of the engagement. Demonstrable progress reports and evidence will be provided throughout the journey for both senior executives and technical teams.
What are some of the services within MISS?
CAT’s IT security specialists will work alongside your existing IT team performing tasks such as:
- Ongoing IT security audits
- Essential Eight (E8) assessments, support and maturity uplift
- Implementing effective identity & access management (IAM)
- Enforcing multi-factor authentication (MFA) where possible, whilst strengthening with physical tokens, such as YubiKey
- Enhancing password hygiene (including fully managed LastPass environments)
- Configuring and securing systems
- Reporting back to the business on the security uplift, plus much more
Do I still need my existing IT support team?
Yes! MISS does not replace your existing IT support team.
- MISS will not replace your day-to-day IT requirements
- MISS is not a one-off security project
- MISS is not the implementation of a specific technology
MISS has been designed to complement your existing IT support structure. Your existing IT support team will still be required to do all the tasks they currently do including helpdesk, day-to-day IT administration, equipment management and IT Projects.
Keen to learn more about how MISS?
Contact us today to speak with one of our specialists and discover how our Managed IT Security Services (MISS) can support your company’s security maturity journey.